- Why are longer passwords better?
- A bigger Haystack – 11 to 12 characters
- Let’s go bigger – 18 characters
- Better Longer Passwords – 25 characters
- Password Managers
1. Why are longer passwords better?
A good strong password can be thought of as hiding a needle in a haystack. You first look around the edge of the haystack just in case the needle is bright red and the size of a knitting needle! But you soon realise that you just need to roll up your sleeves and dive into the stack. Ultimately you find that you aren’t making any progress with your random hand grabbing. You therefore sit down and methodically start removing each hay stem one at a time and check to see if it is a needle. It is boring and if someone has given you a really big haystack then it is going to take you a very long time to find that elusive needle!
This can be the same with passwords. Once you have tried all the most common (“easy pickings”) passwords and dictionary words, a password hacker will have to eventually turn to a “brute force” attack – ie trying every possible combination of letters, numbers and symbols until a match is found. That is why a longer password is always going to be better, because longer passwords are hidden inside very large haystacks.
“If every possible password is tried, sooner or later yours will be found.
The question is: Will that be too soon . . . or enough later? ” – Steve Gibson (GRC.com)
Steve Gibson from GRC has a useful website which helps to explain how longer passwords can stand up against a Brute Force password attack.
Below are screenshots taken from the Gibson Research Corporation (GRC.com) – https://www.grc.com/haystack.htm
PLEASE NOTE – Do NOT use the GRC haystack webpage as a place to check the strength of your real life passwords. The Haystacks site is purely an example of mathematical computation; starting from a lowercase “a” and counting up through all the lowercase letters, uppercase letters, numbers and special characters in each physical placeholder location.
For example – a Brute Force attack would check all character combinations and placeholder positions :
“a” to “aa” to “aaa“, on to “aAA“, then “aAZ” to “aABCZZ().##”
to something like “aA###r###Yj###3##1#########a####A###xX####9##0#####L########“
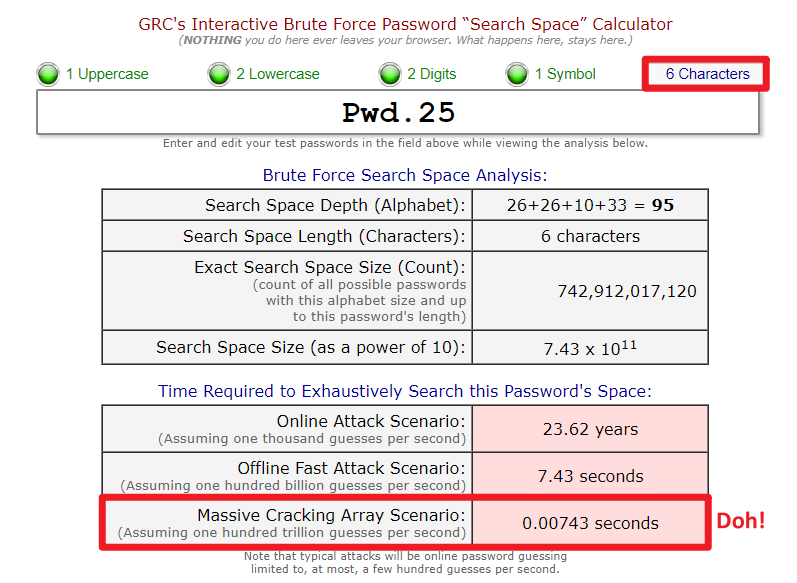
As of today (24 June 2020**) the University’s minimum password length is 6 characters and must include at least three out of four character sets (uppercase, lowercase, numbers and special characters). As you can see from the screenshot below from the GRC haystacks website an offline Massive Cracking Array Brute Force attack would be no competition.
**Update – The University has since improved its account security to a minimum 16 characters together with Multi-Factor Authentication (MFA).
At one hundred trillion guess per second – the Massive Cracking Array may seem a little far fetched, but these are the numbers which are now possible. Obviously, any online system would block that sort of abusive attack, so therefore an online attack might be restricted to just a few hundred guesses a second or hour.
What I’m trying to say is that you should really consider a short length password as being already compromised. Hacking systems these days use password dictionaries, rainbow tables and hashes to target systems. If your current password has less than 12 characters then you should consider it to be available in a hacker’s electronic password dictionary which are freely downloadable from the Dark Web.
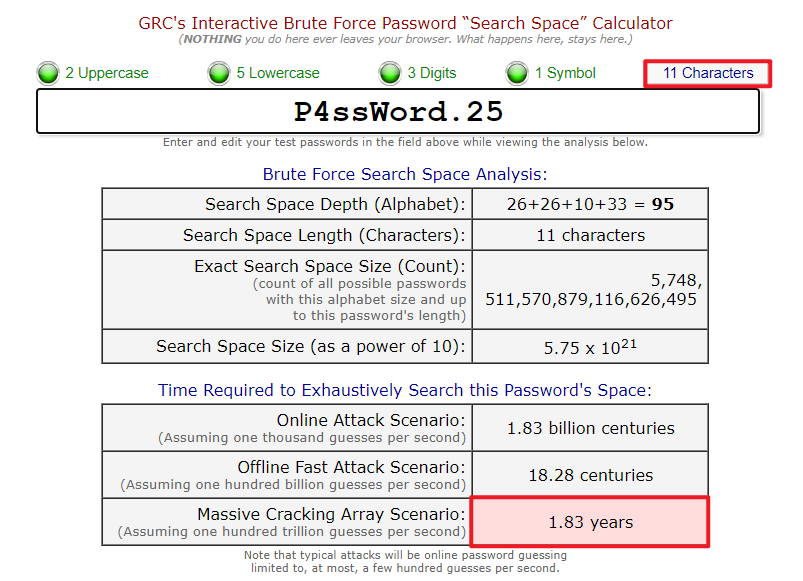
2. A bigger Haystack – 11 to 12 characters
You really see a dramatic improvement in hacking times when going from an 11 character password to 12 characters. It is the difference between years to crack a password to centuries.
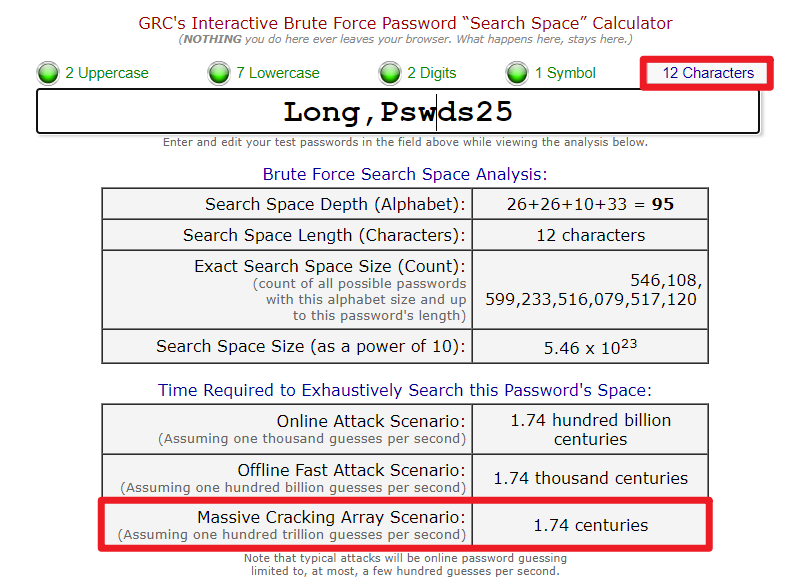
3. Let’s go bigger – 18 characters
Now this is what I mean by a large haystack. We are now in the region of trillions of centuries.
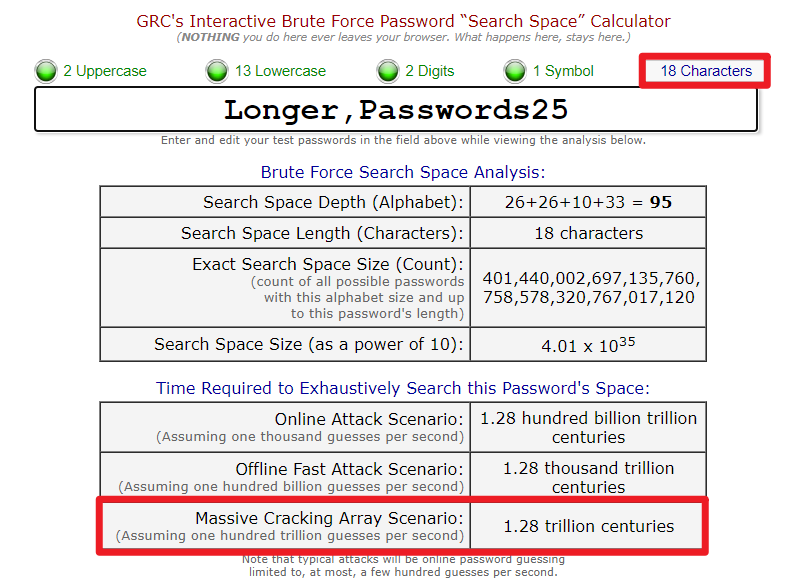
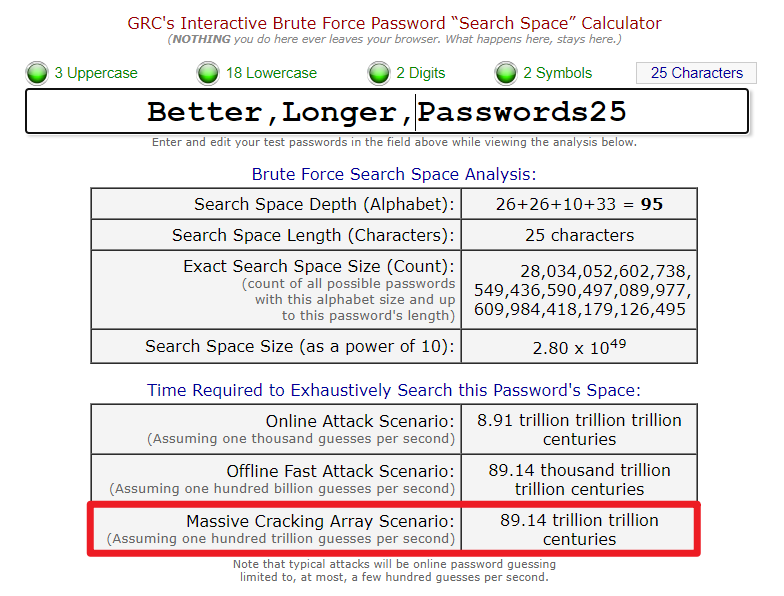
4. Better Longer Passwords – 25 characters
Of course, long passwords are a fantastic idea but how are you supposed to remember them? You might be tempted to write your beautiful long password down in a safe place? But as soon as your password is compromised – found on a Post-it note left under a keyboard, handwritten note in the back of a diary – or more likely – you type it into a compromised server or you follow a fake web link in an email and provide the hackers with your precious password. In these cases the hackers don’t need to crack your password. You just gave it to them on a silver tray!
No matter how long the password is – if you give it away then you are in a compromised position.
5. Password Managers
So, having longer passwords then leads to the question – How do you remember longer passwords?
That is why we recommend that you consider a Password Manager which can be installed on your computer, web browser and smartphone. A Password Manager also associates the web site with the password. This means that should you visit a fake website then the password manager would not recognise the website address and therefore would not offer you a password, thereby informing you that you are not at the correct web site.
Some well-known Password Managers are 1Password, BitWarden, KeyPass to name a few but there are many more. For a useful resource to learn more about Password Managers then visit https://www.passwordmanager.com and review their list of Password Managers based on research and reviews – https://www.passwordmanager.com/best/